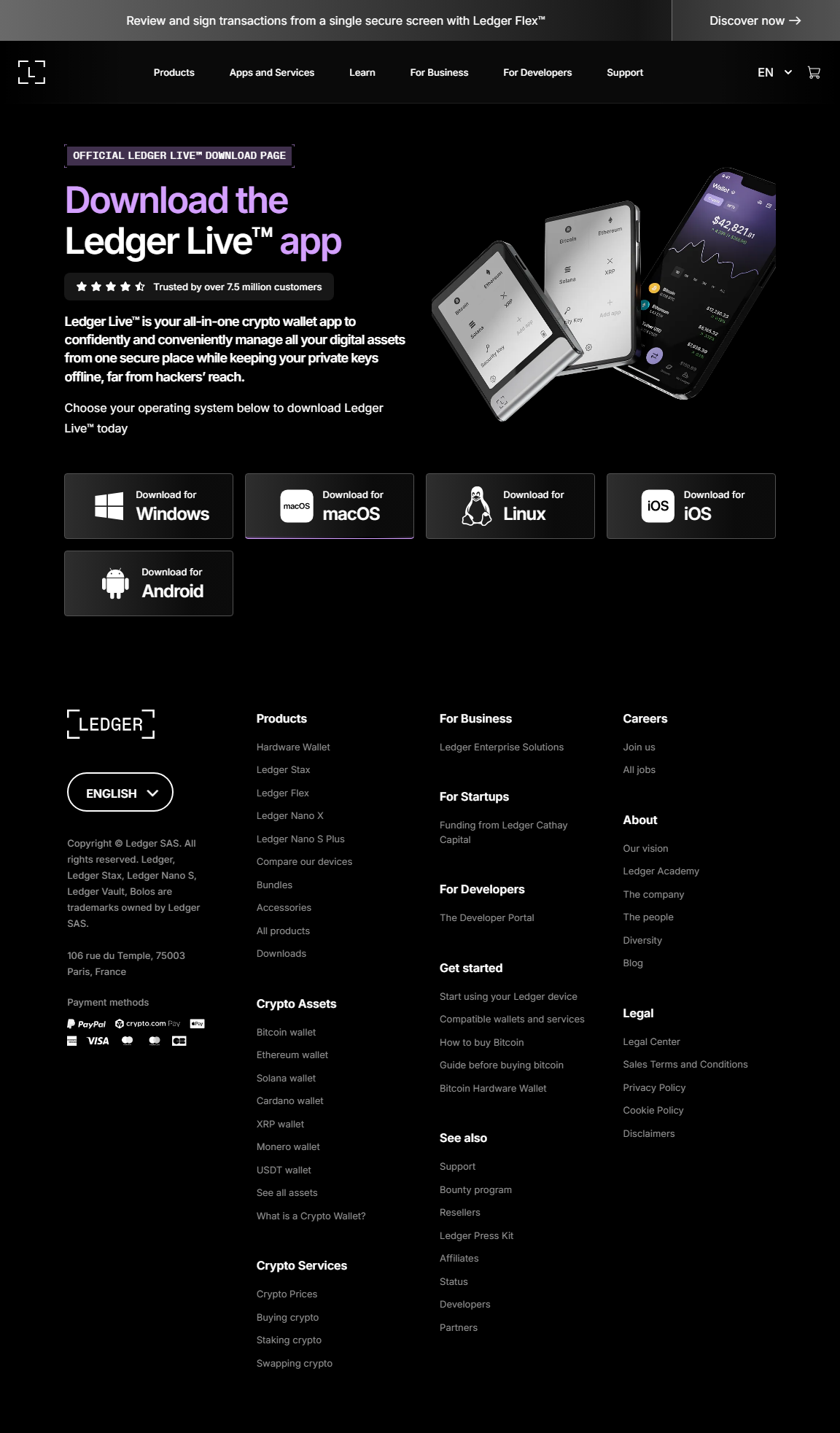
Ledger Live Login: Secure Access to Your Crypto Universe
The complete guide to authenticating with your Ledger device and managing assets securely
Understanding the Ledger Live Authentication Model
Ledger Live login represents a revolutionary approach to cryptocurrency access that eliminates traditional password vulnerabilities. Unlike conventional financial apps that rely on cloud-based authentication, Ledger Live uses a hardware-first security model where your physical Ledger device becomes your identity. This decentralized authentication ensures that your private keys and sensitive data never leave the secure environment of your hardware wallet.
The login process creates a secure bridge between the user-friendly Ledger Live interface and the iron-clad security of your Ledger device, allowing you to manage your portfolio while maintaining complete control over your private keys.
The Step-by-Step Authentication Process
Application Launch
Open Ledger Live on your desktop or mobile device. The application scans for available Ledger devices and prepares for secure connection.
Device Connection
Connect your Ledger device via USB or Bluetooth. Enter your PIN directly on the device—this input never touches your computer.
App Selection
Navigate to and open the specific cryptocurrency application on your Ledger device for the assets you want to manage.
Secure Session
Ledger Live establishes an encrypted session, allowing you to view balances and prepare transactions while keeping private keys secure.
Security Features Protecting Your Login
Hardware-Enforced Authentication
Ledger Live's security model is built around the principle that private keys never leave your hardware device. The secure element chip in your Ledger generates and stores keys in complete isolation, making them immune to computer malware, phishing attacks, and remote exploitation. Every operation requiring private key access must be physically confirmed on the device itself.
PIN Protection & Auto-Lock
Your Ledger device implements sophisticated PIN protection with automatic wiping after consecutive failed attempts. Both Ledger Live and your hardware device feature auto-lock functionality, ensuring that your session remains secure even if you step away from your computer. The PIN is verified locally on the device and never transmitted to your computer.
Troubleshooting Common Login Issues
Connection Problems
Try different USB cables and ports. Ensure you have the latest Ledger Live version and that your device firmware is updated. Restart both the application and device.
Device Not Recognized
Check if your Ledger is in bootloader mode. Ensure no other cryptocurrency applications are running that might be blocking access to your device.
Mobile vs Desktop Login Experience
Platform-Specific Features
- Desktop: Full portfolio management, trading features, and detailed analytics with direct USB connection for maximum security
- Mobile: Balance checking, transaction history, and notifications with Bluetooth connectivity (Nano X) for on-the-go access
- Both Platforms: Same security model with hardware-based authentication and PIN protection
- Automatic synchronization between devices when using the same Ledger device
The Future of Secure Crypto Access
Ledger Live login represents the gold standard in cryptocurrency security, combining the convenience of modern software with the uncompromising protection of hardware wallets. By eliminating traditional password vulnerabilities and keeping private keys completely isolated in secure hardware, Ledger has created an authentication system that protects against both digital and physical threats. As the cryptocurrency ecosystem continues to evolve, this hardware-based approach to login security will become increasingly essential for anyone serious about protecting their digital assets in our interconnected world.